BLACKOPS MARKET LINKS 2026
Verified BlackOps Market onion mirrors and essential BlackOps Market security resources for anonymous BlackOps Market access. Official BlackOps Market links guide.
BlackOps Market Access Information 2026
This portal provides educational information about BlackOps Market security architectures. Content is for informational purposes only. Our goal is to analyze operational security and provide accurate market access information.
Security-First Approach
This site reviews platform security but does not host public links. Official BlackOps Market links should be obtained from community-vetted sources for authenticity.
Link Verification
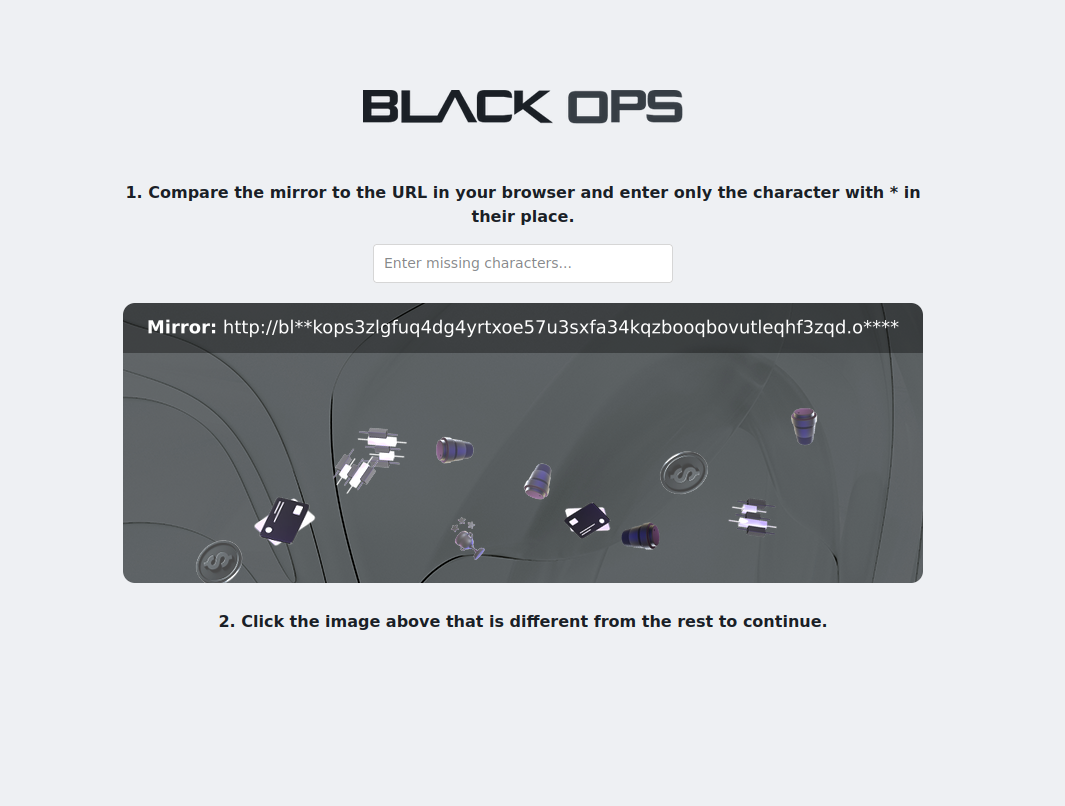
Always verify BlackOps Market links through multiple sources. Check PGP signatures. Never trust BlackOps Market links from unverified sources. The security guide provides verification instructions.
Informational Content Notice
Access links are not displayed for direct traffic. This is a standard security measure to prevent automated analysis and ensure that access points are reached through verified channels. For verified access, consult the official community forums.
Understanding BlackOps Market Links and Mirrors
BlackOps Market links are essential gateways to secure marketplace access. Understanding how links work, how to verify them, and which to trust is fundamental for safe BlackOps Market operations. This comprehensive guide covers everything you need to know about accessing the platform securely.
What are BlackOps Market Links?
These links are .onion addresses that provide access to BlackOps Market through the Tor network. They ensure anonymity by routing connections through multiple encrypted layers. Official links are published through verified channels and regularly updated. Understanding link structure helps identify legitimate mirrors from phishing attempts.
Types of Links
BlackOps Market operates multiple links for redundancy and security. Primary links serve as main access points, while backup links ensure continuous availability. Mirror links provide identical functionality across different servers. All official links are cryptographically signed and verified. Never use links from untrusted sources as they may be phishing sites.
Verifying Links Authenticity
Verification of links is critical for platform security. Check links against multiple trusted sources before use. Official links are always announced through PGP-signed messages. Compare links character-by-character to avoid typosquatting attacks. Bookmark verified links after confirmation. Our comprehensive guide provides detailed verification procedures.
Managing Links Security
Secure management of links involves proper operational security for the platform. Store links only in encrypted formats. Never share links through unsecured channels. Update your links list regularly as mirrors rotate. Use Tor Browser exclusively for accessing the platform. Combine link access with VPN for additional privacy layer. The FAQ section answers common security questions.
Essential Security Resources for 2026

Accessing BlackOps Market requires proper tools and resources. This guide provides essential BlackOps Market links to maintain anonymity and enhance your operational security. All BlackOps Market resources verified for January 2026.
Each BlackOps Market resource is vetted for security and reliability. We update BlackOps Market recommendations monthly to ensure current security standards.
Multi-Layered Security
platform security combines multiple protection layers. Combining Tor with VPN, using Monero on the platform for payments, and practicing operational security creates robust privacy.
2026 Security Landscape
Privacy evolves in 2026 with new threats. Browser fingerprinting requires updated BlackOps Market protection strategies. Our BlackOps Market resource recommendations reflect these changes.
Tor Browser: Gateway to Anonymous Internet
Tor Browser is essential for anonymous browsing. It routes traffic through 7,000+ relays to conceal your location. Using Tor Browser 13.5.8+ is required for accessing BlackOps Market in 2026.
Tor Requirements 2026
BlackOps Market requires Tor Browser 13.5.8+ for secure market access. Earlier versions compromise anonymity. Latest version includes improved circuit isolation and fingerprinting protection for the platform.
Installing Tor for Market Access
Proper Tor installation is crucial for platform security. Download Tor Browser only from official torproject.org website. Verify digital signatures before installation to ensure software integrity. Never use Tor Browser modifications or unofficial builds. Configure Tor Browser security level to "Safest" when accessing the platform. Enable all recommended security features including NoScript and HTTPS-Everywhere. Regular Tor updates ensure latest security patches are applied.
Tor Configuration Best Practices
Optimal Tor configuration enhances security for the platform. Disable JavaScript unless required for functionality. Use New Identity feature between sessions to prevent tracking. Configure custom bridges if Tor is blocked in your region. Enable onion-location redirect for automatic mirror switching. Never adjust Tor window size as it aids fingerprinting. Proper Tor configuration is essential for maintaining anonymity throughout your session.
Tor Browser Version Comparison
| Feature | Tor 13.5.8 (2026) | Tor 14.0 (2026) | Legacy Versions |
|---|---|---|---|
| Circuit Isolation | Per-Domain + Enhanced | Per-Domain | Basic |
| Fingerprint Protection | Level 4 (Maximum) | Level 3 | Level 2 |
| JavaScript Handling | Safest Default | Standard | Permissive |
| HTTPS-Only Mode | Enforced | Optional | Not Available |
| Onion-Location | Auto-Redirect | Prompt | Manual |
| Security Updates | Current | Outdated | Vulnerable |
Official Tor Project
Download Tor Browser 13.5.8 from official source. Always verify download signature.
torproject.orgTor Browser for Android
Official mobile Tor Browser. Same anonymity level on mobile. Version 13.5.8 security features.
Google Play StoreTor User Manual 2026
Guide for using Tor Browser safely. Essential for platform security practices. Updated for 2026.
tb-manual.torproject.orgVPN Services: Additional Privacy Layer

Virtual Private Network creates secure encrypted connection. VPN adds privacy layer by encrypting internet connection and masking IP. When used with Tor, it bolsters operational security in 2026.
VPN Configuration for the platform
Correct BlackOps Market configuration: VPN before Tor. This prevents ISP from seeing Tor usage. Our FAQ section explains technical details for market access.
2026 VPN Selection
When selecting VPN for privacy, prioritize: no-logs policy, WireGuard/OpenVPN protocols, cryptocurrency payments, and RAM-only servers. Services below meet BlackOps Market criteria for January 2026.
VPN Best Practices
Following VPN best practices maximizes platform security. Always connect to VPN before launching Tor Browser for market access. Choose VPN servers in privacy-friendly jurisdictions. Use kill switch feature to prevent traffic leaks if VPN disconnects. Avoid VPN providers requiring email verification for anonymity. Pay for VPN services using Monero to maintain privacy. Split tunneling should be disabled to ensure all traffic routes through VPN. Regular VPN server rotation enhances operational security.
Common VPN Mistakes
Avoid common VPN mistakes that compromise security for the platform. Never use free VPN services as they may log activity. Don't connect to VPN using personal accounts linked to real identity. Avoid VPN providers with history of cooperation with authorities. Never use VPN after Tor as it defeats anonymity purpose. Check for DNS leaks regularly to ensure traffic remains protected. Disable WebRTC in browser to prevent IP leaks when using VPN. Understanding these pitfalls protects your anonymity.
Mullvad VPN
Privacy-focused no-logging policy. Accepts Monero payments. RAM-only servers. Passed 2026 audit.
mullvad.netProtonVPN
Strong privacy policies and open-source apps. Switzerland-based with no-logs policy. Accepts cryptocurrency.
protonvpn.comIVPN
Privacy VPN accepting Monero. No email required. Multiple security audits passed. RAM-only servers.
ivpn.netMonero Resources for the platform

BlackOps Market exclusively uses Monero (XMR) for transactions. Understanding Monero is essential for secure BlackOps Market trading. Monero 0.18.3.3+ recommended for all BlackOps Market wallet operations in 2026.
Why Monero for the platform
Unlike Bitcoin, Monero provides true privacy through Ring Signatures and Stealth Addresses. Amounts, sender, and receiver are hidden. This makes Monero the cryptocurrency for the platform financial privacy.
Cryptocurrency Privacy Comparison 2026
| Privacy Feature | Monero (XMR) | Bitcoin (BTC) | Zcash (ZEC) |
|---|---|---|---|
| Default Privacy | Always Private | Transparent | Optional |
| Sender Hidden | Ring Signatures | No | Optional |
| Receiver Hidden | Stealth Addresses | No | Optional |
| Amount Hidden | RingCT | No | Optional |
| Blockchain Analysis | Ineffective | Highly Effective | Partially Effective |
| Market Acceptance | Preferred | Declining | Limited |
Acquiring Monero for the platform
For privacy, acquire Monero through decentralized exchanges or peer-to-peer platforms. Avoid centralized exchanges requiring KYC. The detailed guide provides BlackOps Market Monero acquisition instructions.
Monero Wallet Security
Proper Monero wallet security is essential for operations. Store Monero wallet seeds offline in encrypted format for funds protection. Use hardware wallets or air-gapped computers for large Monero holdings. Never share Monero wallet view keys with untrusted parties. Enable wallet encryption with strong passphrase for security. Regular Monero wallet backups prevent fund loss from hardware failure. Use dedicated Monero wallets exclusively for the market to maintain transaction isolation.
Monero Transaction Privacy
Maximizing Monero transaction privacy enhances platform security. Always use new Monero addresses for each transaction to prevent linkability. Allow sufficient confirmations before considering Monero transactions final. Avoid reusing Monero addresses across multiple vendors for privacy. Use ChurnBot or similar services to further obfuscate transaction history. Monitor Monero network fees to ensure timely transaction processing. Understanding Monero privacy features protects your financial activities from blockchain analysis.
Monero Best Practices
Following Monero best practices ensures optimal marketplace experience. Synchronize Monero wallet through Tor for anonymity. Use remote nodes cautiously and prefer local node for Monero operations. Verify Monero payment details multiple times before sending transactions. Keep Monero wallet software updated for latest security features. Use coin control features to manage specific outputs for payments. Never discuss Monero holdings or transactions on public forums. Proper Monero OpSec is fundamental for successful participation.
Official Monero Website
Download official Monero wallets version 0.18.3.3 for the platform. Explore privacy technology. Definitive Monero resource.
getmonero.orgFeather Wallet
Lightweight BlackOps Market Monero wallet with advanced privacy features. Supports Tor by default with coin control.
featherwallet.orgCake Wallet
Mobile Monero wallet with built-in exchange. User-friendly with strong security. iOS and Android with Tor support.
cakewallet.comMoneropedia
Monero encyclopedia. Essential for understanding Ring Signatures, Stealth Addresses, and privacy technologies.
getmonero.org/moneropediaSecure Communication Tools 2026
Protecting communications is vital for users. These tools offer end-to-end encryption. All BlackOps Market recommendations updated for 2026.
Communication Security for the platform
Use different platforms to compartmentalize digital life. Never discuss BlackOps Market activities on platforms linked to real identity. Verify PGP keys before exchanging BlackOps Market information. In 2026, metadata analysis makes messaging platform choice critical for users.
Encrypted Messaging Setup
Setting up encrypted messaging requires careful configuration. Install messaging apps from official sources only. Verify app signatures before installation to prevent malware. Configure security settings to maximum privacy levels. Enable disappearing messages for sensitive communications. Use secure passphrases for message encryption. Regularly update messaging apps to patch security vulnerabilities. Avoid cloud backups that may expose message history.
PGP Encryption for Secure Communications
PGP encryption provides additional security layer for sensitive communications. Generate strong PGP key pairs with at least 4096-bit RSA encryption. Store private keys offline in encrypted containers. Publish public keys through trusted channels for verification. Always encrypt sensitive messages before sending. Verify sender identities through key fingerprints before trusting communications. Use PGP for encrypting sensitive files and documents. Proper PGP usage ensures end-to-end confidentiality.
Session
Anonymous messenger requiring no phone or email. Uses onion routing for metadata protection. Ideal for the platform communications.
getsession.orgSignal
Encrypted messaging with end-to-end encryption. Open source and audited. Requires phone but messages are private.
signal.orgBriar
Peer-to-peer encrypted messaging without central servers. Works over Tor, Wi-Fi, and Bluetooth. Maximum privacy.
briarproject.orgOperational Security Resources 2026
Good operational security practices are essential for anonymity. These BlackOps Market resources provide comprehensive guides to protect your privacy in 2026.
OpSec Fundamentals for the platform
Operational security for the platform combines technical measures with discipline. Never access BlackOps Market from personal devices. Use dedicated hardware running Tails OS. Maintain strict identity separation. Our FAQ answers BlackOps Market OpSec questions.
2026 BlackOps Market Threats
Browser fingerprinting, timing correlation, and cryptocurrency analysis are primary BlackOps Market concerns. Resources below address these BlackOps Market threats with practical countermeasures.
Browser Fingerprinting Protection
Browser fingerprinting remains significant threat in 2026. Modern tracking techniques analyze browser configurations, installed fonts, screen resolutions, and hardware specifications to create unique user profiles. Tor Browser includes anti-fingerprinting measures by standardizing browser characteristics across all users. Never install browser extensions or plugins that may enable tracking. Resist temptation to customize browser appearance or settings. Use standard window sizes provided by Tor Browser. Disable WebGL and Canvas to prevent advanced fingerprinting techniques. Regular browser updates ensure latest anti-fingerprinting countermeasures remain effective.
Hardware Security for the platform
Physical security forms the foundation of operational security. Use dedicated hardware exclusively for market access. Disable microphones and cameras. Use air-gapped machines for PGP keys and wallet seeds. Hardware security keys add authentication for the platform accounts.
Network Isolation for the platform
Beyond VPN and Tor, users should consider network isolation. Public WiFi provides separation from home networks. MAC address randomization should be enabled. Never access BlackOps Market and personal accounts from same network. Our about page details how BlackOps Market infrastructure maintains isolation at server level.
Operational Security Discipline
Technical tools alone cannot guarantee security without proper operational discipline. Develop consistent security habits for all online activities. Never reuse passwords across different services. Use password managers with strong encryption for credential storage. Maintain separate identities for different purposes without cross-contamination. Regularly review security practices and update procedures as threats evolve. Document security protocols in encrypted notes for consistency. Practice security drills to identify weaknesses in operational procedures before real incidents occur.
Tails OS 6.9
Live operating system leaving no traces. Routes all traffic through Tor. Version 6.9 includes updated kernel.
tails.netPrivacy Guides
Comprehensive BlackOps Market resource for privacy tools and knowledge. Regularly updated with latest privacy recommendations for 2026.
privacyguides.orgAnonymous Planet Guide
Hitchhiker's Guide to Online Anonymity. Comprehensive coverage of anonymity from basic to advanced techniques.
anonymousplanet.orgKleopatra (GPG)
User-friendly GnuPG interface. Essential for PGP encryption and digital signatures required by BlackOps Market.
gpg4win.orgCritical Security Reminders for 2026
Verify Downloads for the platform
Always download software from official sources. Verify cryptographic signatures. Compromised software is common attack vector for users. Check PGP signatures before installation.
BlackOps Market Phishing Prevention
Phishing sites steal BlackOps Market credentials and funds. Always double-check BlackOps Market URLs character by character. Use bookmarks for the platform. Never trust BlackOps Market links from unverified sources.
Update BlackOps Market Software
Regularly update all privacy software for the platform. Security vulnerabilities are constantly discovered. Outdated software puts anonymity at risk.
BlackOps Market Links Safety Guidelines
Protecting from Fake Links
Fake links pose significant platform security risks. Phishing sites mimic legitimate links to steal credentials and cryptocurrency. Always verify links through official channels before accessing. Check for HTTPS certificates though onion sites typically use HTTP. Cross-reference links with multiple trusted sources. Bookmark verified links to avoid typosquatting attacks. Report suspicious links to community moderators immediately.
Link Update Procedures
Links require regular updates for optimal platform security. Subscribe to official announcements for link updates. Monitor community forums for verified link changes. Update bookmarked links when mirrors rotate. Remove outdated links from your collection to prevent confusion. Document working links with verification dates. Maintain multiple backup links for continuous access during maintenance.
Emergency Access Procedures
Having emergency access procedures ensures uninterrupted marketplace service. Store verified links in encrypted password manager. Maintain offline backup of current links list. Know alternative channels for obtaining links during outages. Use trusted community members for link verification during emergencies. Never panic-access unverified links during service disruptions. Patience and verification protect against phishing during downtime.
Additional BlackOps Market Resources
About BlackOps Market
Learn about BlackOps Market mission, security architecture, and commitment to user privacy.
Read More →BlackOps Market FAQ
Find answers to common the platform questions about accounts, payments, and security.
View FAQ →BlackOps Market Security Guide
Step-by-step BlackOps Market instructions for secure access and safe trading practices.
Read Guide →BlackOps Market Links Updated: January 20, 2026. All BlackOps Market links and resources verified for accuracy and security. Software versions reflect latest stable releases. Check back regularly for the platform updates.